On the 29th of September 2020 I managed to take over a subdomain of a Middle school in the Netherlands. The funny part being the fact that I was simply testing a tool that I’ve written!
During my studies I’ve followed a minor in cyber security, which made me interested in Bug bounty challenges. Rather than challenging myself against bug bounty platforms like Hackerone, I decided to look for other companies which have a responsible disclosure policy.
I often find myself looking at reports of other people to see what kinds of vulnerabilities exist to see if I can perhaps learn new methodologies or about new kinds of vulnerabilities. I happened to come across the “Subdomain take over” vulnerability several times and thought of a way to automate a process to scan a domain for the vulnerability. Little did I know I would find such a vulnerability during one of my first test runs.
Here’s the story.
What is a subdomain takeover?
Before the “how did we get there”, let’s talk about subdomain take overs and what are they?
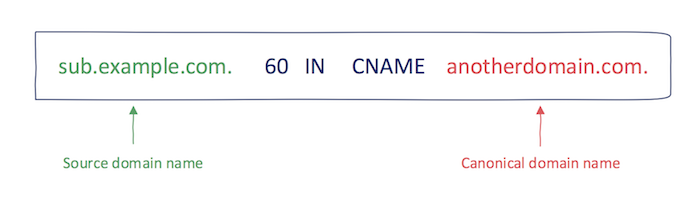
In short, a subdomain take over is exactly what it sounds like, you take over the content that is hosted under a subdomain. However, there is a very specific condition in order to exploit this vulnerability. Most Subdomains which are eligible for take over have a CNAME record, which points a removed or unclaimed virtual host. Some providers of virtual hosts make it possible to claim the host names which have been claimed prior. When an attacker registers a host name which is being pointed to by a CNAME DNS record, the attacker will have control over what is hosted under that subdomain.
Note:
Although take over of other records is possible, the risk is low for it’s unlikely someone will be able to claim a very specific IP address.
How did I find it?
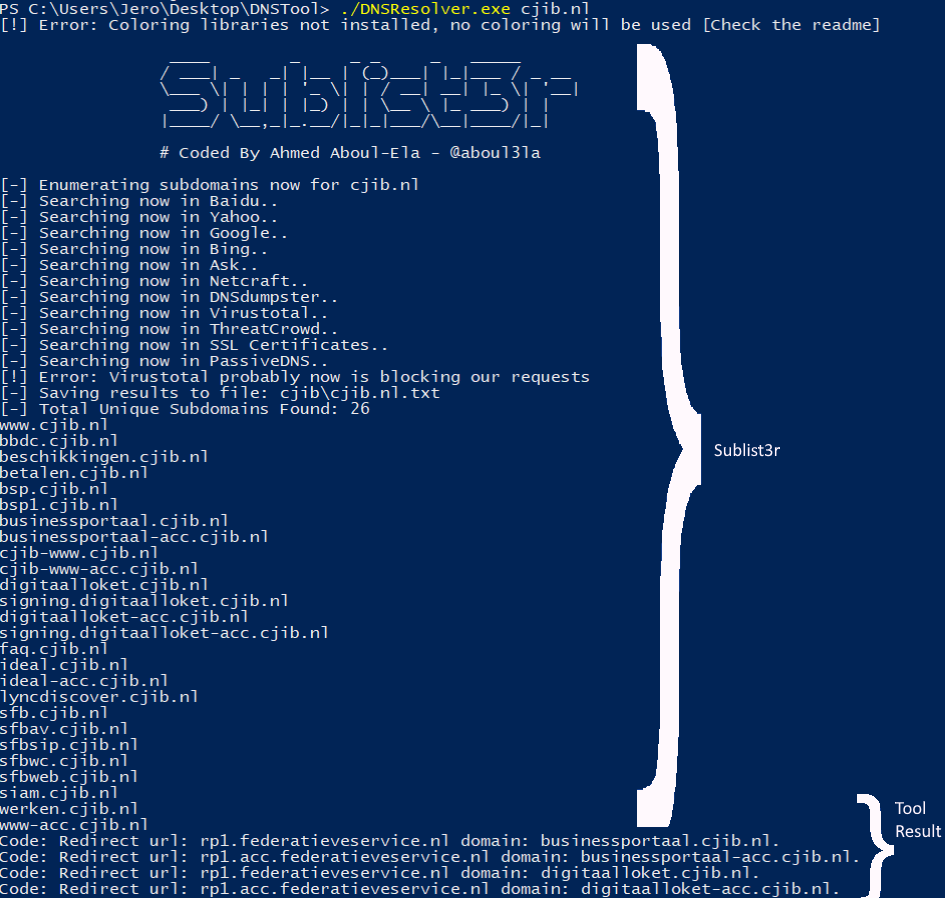
By using a tool which goes by the name of Sublist3r, subdomains can be found. However, this tool only does that, it finds subdomains indiscriminately. This means that all of the subdomains need to be resolved to see if it has a CNAME record attached. Even when you have that uncovered you still need to check if the record is dangling by visiting the URL and checking the status code. The steps just described have not yet been automated as far as I’m aware. So, I decided to write my own tool around sublist3r.
Instead of porting the code over or extend the project in python I decided to just do a quick and dirty build in order to see if it can be done, an MVP if you will. This MVP would do the following:
- The program would call sublist3r and save its findings to a text file. Sublist3r has an option which allows it to save clean entries.
- All the subdomains would get resolved through a DNS check, however only the CNAME records would be saved
- All the resolved canonical names would get visited. Those with another status code than 400 would get printed out for manual checking.
The image below shows an example of a website hosting a privacy statement which essentially allows me to scan their website.
In the real world practice, I was debugging the application. I had run into some errors which I was looking through in debug mode. I stumbled on a request with status code 410, GONE. I looked at the created table and found that the record pointed to an azure website. I used my Azure trial and tried to register the name…
Bingo.

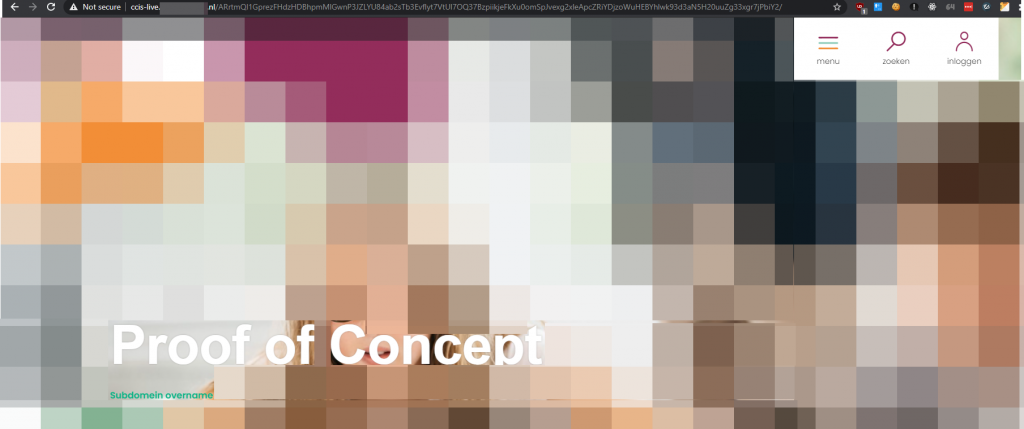
I registered the website; visited their subdomain and got a 400 status code which pointed to an azure website. I used a HTTrack to copy their frontpage; edited some of the text on the page and published it on the website. A route was created with an unguessable name, which showed the implications of the takeover. The blurred image below was a screenshot of the end-result. The image is blurred because although I received permission to publish the issue, I was asked not to publish direct links.
In the off chance someone would find the website, I made sure the base route would redirect the user to the main website.
Did I get anything?
After the exploitation I sent an email to their security team explaining that their subdomain has been taken over, what has been done and how to resolve the issue. About an hour later I got a reply.

What happened? I was sure I correctly pasted the address. I double checked the address and noticed that it was correctly copied. I did notice something else, there was a typo in their posted e-mail address. I corrected the mistake, resend the email and waited.
The following day I received an email stating: “Thank you for the information, we’re immediately going to take action.” Great! They are going to solve the issue. So, I replied, “Thank you! it’s good to see it’s being taken seriously.” To which I got a response “It was little effort, thank you again for reporting the issue.”. At this point I got confused, their Responsible disclosure document states that a bounty would be awarded based on the severity of the issue; was it not seen as a serious threat? I sent another email stating that I had a few more questions regarding publication and addressed the bounty clause. I stated that the complexity of fixing the issue should not be equivalent to the consequences a problem could cause. I received a response stating that the responsible disclosure document wasn’t on his mind anymore, because he hadn’t received any messages thus far.
After some discussion he’d offer me a gift card of €50, not wanting to ask for too much, I agreed. A few days later I received a personal letter in the mail, along with the promised gift card, and some swag.
What is next?
The Subdomain tool that I’ve written was an MVP, it does what it needs to, but has too many quirks. For instance, it’s a tool which calls another tool; then uses those results to perform extra steps. There are a few changes that I want to make:
- I want to port Sublist3r’s code so that the tool can be completely integrated.
- I want to be able to automatically check whether the domain can be registered
- I want to be able to scan domains which hold a responsible disclosure document
Thank you for reading!